Information has always been valuable. Probably never more than today. That is why it needs to be protected. But what do information security and its relative cybersecurity really mean? SRS sorts out the concepts.
What does information security mean?
Information in various forms is needed in order to carry out all kinds of business activities. It can also be valuable for other reasons; from life-critical information in patient records and control of electricity distribution to images and the results of a research project. If the information falls into the wrong hands, changes, or is lost, it can cause great harm to individuals and companies. Information security also has special importance as a protective security measure in the Security Act (2019:585).
Therefore, in our increasingly digitized world, there is a great need for organisations to work with information security. It is mainly a question of protecting information from being:
- accessed by unauthorized (confidentiality)
- destroyed or made unavailable (availability
- changed without being detected (accuracy)
How should companies work with information security?
Information security is a step in the process of securing a company’s assets. This may include, for example, the establishment of administrative guidelines and policies for IT systems, but in order for information to be optimally protected, a more holistic approach to security needs to be adopted. For a modern company, routines and processes for safety management, personnel safety, and physical protection also need to be reviewed.
The task for SRS regarding information security, the goal not only to protect company information. We apply the SRM model, Security Risk Management, to protect a company’s overall key assets against any industry-specific threats. Key assets vary from company to company. They may include staff, public image, and financial resources. The company’s facilities, the ability to deliver services, and the information worthy of protection can also be included. The protection of all key assets is made possible by the SRM model, which includes security management, people security, physical security, and cybersecurity.
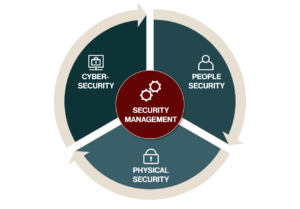
Complement your information security with cybersecurity
Information of any kind is the cornerstone of any business. The information that needs to be protected is often found in humans and on paper, but most commonly today it is stored in IT systems and it is important to preserve the confidentiality of the information so that no unauthorised person can access the information. As an increasing proportion of companies have digitised their services, they risk losing money if their IT systems containing, for example, customer orders and deliveries do not work or suddenly contain changed information. This puts great demand on protecting the availability and accuracy of information.
Unfortunately, it is not enough simply to increase cybersecurity in order to get good information security, an actor can also use an employee as an insider or physically access any part of that network to place hidden access points there. That is why it is important to have a holistic approach to information security through correct cybersecurity, people security, physical security, and security management, as demonstrated by the SRM-model.
SRS often uses the concept of cybersecurity instead of IT security. This is because the concept of IT security is primarily aimed at protecting the IT systems of a company that manages its information assets, which were previously often located on the company’s own premises. Cybersecurity refers to the protection of all the company’s IT systems, wherever they are physically located and whether they are connected to the internet. This includes industrial control systems, lock and alarm systems, access control systems, internet of things (IoT), etc. Briefly explained: without functioning cybersecurity, the company has no possibility of achieving good information security.
Information security with SRS
Let the security company SRS apply a holistic approach to your information security and this way secure all of your key assets based on the SRM model so that you can focus on driving your business forward. Please contact us if you need to improve your information security, and we will lead you right.

